Cybersecurity Best Practices: How We Protect Your Information Together
The news is rife with stories about identity theft and cybersecurity incidents. Every few months, we have a service or company or government agency that reports a data breach that reveals non-public personal information about hundreds of thousands or even millions of records, data like social security numbers, dates of birth, passwords, and account numbers. Criminals use this information to pull off fraudulent transactions, file sham tax returns, or impersonate someone to extract money from those of us who have a trusting nature. Here are a few facts:
$16.9 billion was lost to identity fraud in 2019.
SOURCE: 2020 JAVELIN STUDY ON IDENTITY FRAUD
Scams that start on social media totaled $134 million in losses in 2019.
SOURCE: FEDERAL TRADE COMMISSION
80% of confirmed data breaches involved compromised or stolen passwords.
SOURCE: VERIZON 2019 DATA BREACH INVESTIGATIONS REPORT
94% of malware was delivered by email.
SOURCE: VERIZON 2019 DATA BREACH INVESTIGATIONS REPORT
Clients are naturally concerned, and some are reluctant to share information, rightfully wanting to protect themselves from the emotional and financial turmoil that cybercriminals want to cause. As a result, you might feel reluctant to share information with us. However, to do the best job possible, we need to understand your complete personal and financial situation. That means, the more you share with us, the better able we are to offer you great advice.
We want you to have a healthy skepticism but not be scared. We want you to be confident in your ability to pick out the strategies that would-be lawbreakers are using to acquire your information and laugh in the face of these criminals and the tactics they use. With my background in IT, that’s how I operate, and I hope this article educates you on the practical steps you can take so we can partner together to protect your information.
Ways We Protect You
Here are just a few of the concrete core values and practices that direct us in guarding what you share with us at all times.
As fiduciaries and CFP professionals, we are bound by standards of conduct to be loyal, show care, and maintain the utmost confidentiality. That means none of your personal data is shared with anyone outside our firm except as outlined in our privacy policy.
We have an extensive, ever-maturing cybersecurity program with policies and controls meant to safeguard your data. Our Chief Compliance Officer is responsible for maintaining the program, evaluating our current state, and driving actions that improve safeguards. As part of that program, we’ve done our due diligence to make sure the vendors that operate the technology we use uphold their security responsibilities. Further, and maybe most importantly, our staff is required to complete cybersecurity training annually and to adhere to our policies and procedures.
We don’t send sensitive, non-public information (tax returns, social security numbers, personally identifiable information) through email. We facilitate document exchange through our secure client portal vault and our client document drop-off page. Both avenues provide high encryption, and documents are removed after we retrieve them and at other regular intervals.
We authenticate every transaction request. We don’t execute trade or money movement requests sent via email or text. We have a process in place whereby we verify your identity and transaction details before we take any actions.
Whenever possible, we use electronic signature technology for you to sign paperwork. Not only is this efficient, but our custodian has enhanced capabilities to catch fraud the more we use these e-signing services.
How You Can Stay Safe
I could probably write an article on each and every one of these nuggets of advice below, and the list could certainly be longer. I’ve tried to boil it down to the techniques that will produce the greatest bang for your buck.
Never send personally identifiable information through email. When working with us, always use one of our aforementioned secure methods to exchange documents and sensitive information.
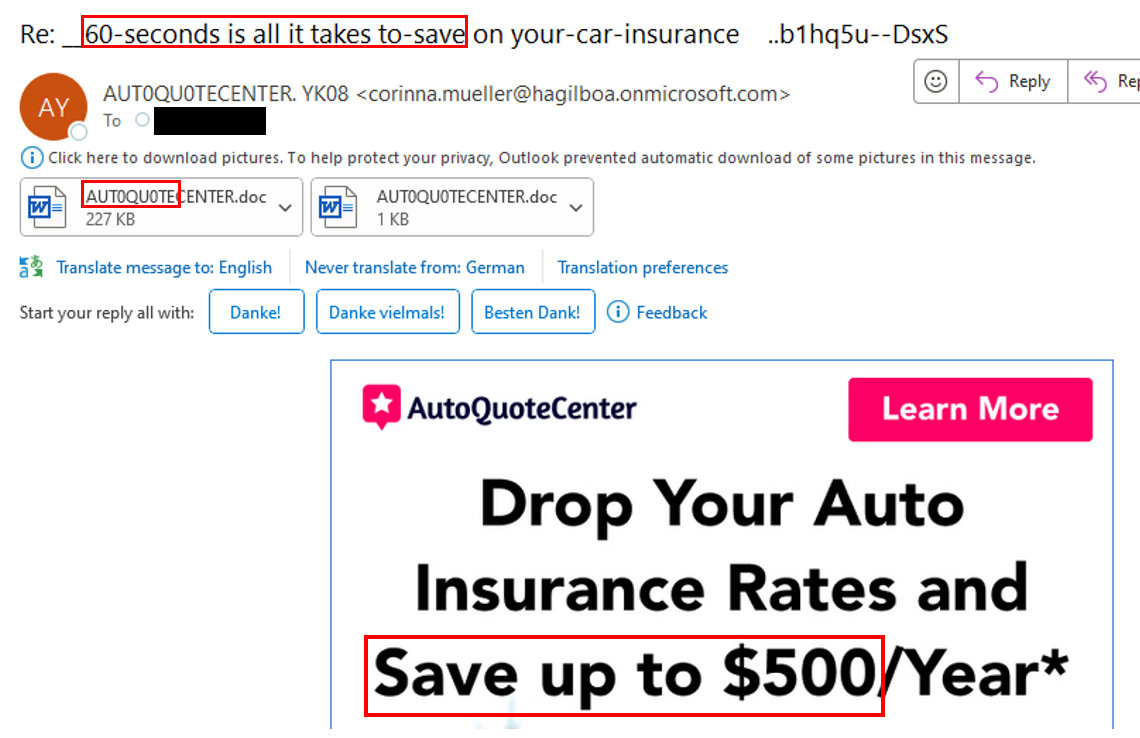
Watch for fraudulent emails that try to appear legitimate. This isn’t your normal legitimate junk-related email. These emails are crafted to look legit. This fraudulent McAfee Antivirus message below is a striking example. In my IT days, I was part of a team whose job was to create genuine looking emails to trick employees as a training exercise to improve their security behaviors.
DO NOT FORWARD THESE MESSAGES TO ANYONE TO ASK IF THEY ARE FRAUDULENT. THAT ONLY SPREADS THE VIRUS. IF SOMEONE ASKS TO SEE WHAT THE EMAIL LOOKS LIKE, TAKE A SCREENSHOT OF THE EMAIL AND SEND THAT INSTEAD.
Validate links on web pages and emails. Seeing an address like the one below that doesn’t match the name purportedly sending you this email is a major red flag, full stop.
NOTICE IN THE ABOVE EXAMPLE THAT THE IMPOSTER (PURPORTED TO BE HARBOR FREIGHT) WANTS THIS EMAIL RECIPIENT TO CLICK A LINK (CONFIRMATION NEEDED), BUT THE UNDERLYING WEBSITE IS CLEARLY NOT RELATED TO HARBOR FREIGHT. YOU CAN SEE THIS BY CAREFULLY HOVERING YOUR CURSOR OVER THE ACTION LINK (BUT DON’T “CLICK OR TAP TO FOLLOW”!).
Be cautious when opening email attachments or downloading files. This is especially so if you weren’t expecting one or aren’t 100% certain of the source. The #1 attack vector I see are malicious attachments that try to pretend to be a legitimate invoice or a useful piece of information. Just don’t open it.
ALWAYS CONTACT THE PURPORTED SENDER (ONLY SOMEONE YOU KNOW!) THROUGH ANOTHER CHANNEL, IDEALLY BY DIRECTLY DIALING THEIR PHONE NUMBER (AND NOT THE ONE IN THE ATTACHMENT OR BODY OF THE EMAIL!) BEFORE DOWNLOADING OR OPENING.
Keep your systems updated with security patches. All major software vendors release security updates regularly (usually monthly) that address known and emerging vulnerabilities. Watch for notifications on your mobile device, smartphone, or computer and apply them as soon as feasible. *60% of data breaches were linked to a vulnerability where a patch was available but not applied. Apply security patches religiously.
*SOURCE: 2019 PONEMON COSTS AND CONSEQUENCES OF GAPS IN VULNERABILITY RESPONSE
Set a complex (upper, lower, number, special) and unique password for each website account. That way, if one site is compromised, the damage is limited. If you use the same simple password across many sites, you increase your chances of one breach leading to others. If it’s complex and long and unique, you don’t need to change it as often. Don’t share your password, either. Managing all of these passwords can be tricky, so I store the unique passwords using secure password management software installed on my computer.
Enable multifactor authentication. This technology requires you to associate your account with your mobile device or email address and sends you a secondary passcode each time you log in. You will especially want to enable this for bank and investment accounts. I personally don’t have this turned on for my utility bills because it’s not that big of a target. What would they do? Pay my bill? However, if any site stores credit card or banking information in a retrievable manner, you ought to consider adding multi-factor authentication.
Limit what you share on social media and make sure your profile is not public. Don’t let the world know your address and that you’ll be out of the country for two weeks in Grand Cayman!
Be aware of the website you surfed to. Everyone has fat-fingered a web address and landed someplace that doesn’t look quite right. Make sure you type the website address correctly into your browser. What about clicking on internet search results? Avoid less well-known sites, links in online posts, or any link on your favorite social media site directing you to purchase tickets to a sold-out Taylor Swift concert at an unbeatable price. (Yeah, I helped someone recover from that last example!)
For even more material for protecting yourself, see these terrific resources:
Industry Resources:
Go to StaySafeOnline.org and review the STOP. THINK. CONNECT.™ cybersecurity educational campaign
Visit OnGuardOnline.gov, also a part of the STOP.THINK. CONNECT.™ campaign, that focuses on online security for kids and includes a blog on current cyber trends
Visit https://www.fbi.gov/scams-safety/fraud to learn more about common fraud schemes
To Report a Cybercrime:
Forward suspicious emails to: nophishing@cbbb.bbb.org
Visit www.identitytheft.gov to report identity theft and to get a recovery plan
Go to FTC.gov for additional consumer resources and to report identity theft
http://www.ic3.gov/default.aspx is another website where you can file cybercrime complaints
No client or potential client should assume that any information presented or made available on or through this article should be construed as personalized financial planning or investment advice. Personalized financial planning and investment advice can only be rendered after engagement of the firm for services, execution of the required documentation, and receipt of required disclosures. Please contact the firm for further information. The content is developed from sources believed to be providing accurate information. The information in this material is not intended as tax or legal advice. Please consult legal or tax professionals for specific information regarding your individual situation. Additional information about The Dala Group, LLC is available in its current disclosure documents, Form ADV, Form ADV Part 2A Brochure, and Client Relationship Summary report, which are accessible online via the SEC’s Investment Adviser Public Disclosure (IAPD) database at https://adviserinfo.sec.gov/firm/summary/291828